IT Services Secure IT Protect myself from phishing
Protect myself from phishing
- Future Students
- JCU Global Experience
- International Students
- Open Day
- How to apply
- Pathways to university
- Virtual Open Day
- Living on Campus
- Courses
- Publications
- Scholarships
- Parents and Partners
- JCU Heroes Programs
- Aboriginal and Torres Strait Islander in Marine Science
- Elite Athletes
- Defence
- Current Students
- New students
- JCU Orientation
- LearnJCU
- Placements
- CEE
- Unicare Centre and Unicampus Kids
- Graduation
- Off-Campus Students
- JCU Job Ready
- Safety and Wellbeing
- JCU Prizes
- Professional Experience Placement
- Employability Edge
- Art of Academic Writing
- Art of Academic Editing
- Careers and Employability
- Student Equity and Wellbeing
- Career Ready Plan
- Careers at JCU
- Partners and Community
- JCU-CSIRO Partnership
- Alumni
- About JCU
- Reputation and Experience
- Chancellery
- Governance
- Celebrating 50 Years
- Academy
- Indigenous Engagement
- Education Division
- Graduate Research School
- Research and Teaching
- Research Division
- Research and Innovation Services
- CASE
- College of Business, Law and Governance
- College of Healthcare Sciences
- College of Medicine and Dentistry
- College of Science and Engineering
- CPHMVS
- Anthropological Laboratory for Tropical Audiovisual Research (ALTAR)
- Anton Breinl Research Centre
- Agriculture Technology and Adoption Centre (AgTAC)
- Advanced Analytical Centre
- AMHHEC
- Aquaculture Solutions
- AusAsian Mental Health Research Group
- ARCSTA
- Area 61
- Lions Marine Research Trust
- Australian Tropical Herbarium
- Australian Quantum & Classical Transport Physics Group
- Boating and Diving
- Clinical Psychedelic Research Lab
- Centre for Tropical Biosecurity
- Centre for Tropical Bioinformatics and Molecular Biology
- CITBA
- CMT
- Centre for Disaster Solutions
- CSTFA
- Cyclone Testing Station
- The Centre for Disaster Studies
- Daintree Rainforest Observatory
- Fletcherview
- JCU Eduquarium
- JCU Turtle Health Research
- Language and Culture Research Centre
- MARF
- Orpheus
- TESS
- JCU Ideas Lab
- TARL
- eResearch
- Indigenous Education and Research Centre
- Estate
- Work Health and Safety
- Staff
- Discover Nature at JCU
- Cyber Security Hub
- Association of Australian University Secretaries
- Services and Resources Division
- Environmental Research Complex [ERC]
- Foundation for Australian Literary Studies
- Gender Equity Action and Research
- Give to JCU
- Indigenous Legal Needs Project
- Inherent Requirements
- IsoTropics Geochemistry Lab
-
IT Services
- Student IT Essentials
- Staff IT Essentials
- Help and Support
- Stay Informed
-
Secure IT
- Choosing a strong Password
- Cyber Security Hub
- Data Protection
- Device Security
- Email Safety
- Online Security at Home
- Web Safety
- Malware and Virus Protection
- Keep a clean device
- Protect myself from phishing
- Recover a hacked or compromised account
- Protect your digital reputation
- Report a cybersecurity incident
- Password Manager
- Multi-Factor Authentication (MFA)
- Student Systems
- IT Service Catalog
- About
- JCU Webinars
- JCU Events
- JCU Motorsports
- JCU Sport
- Library
- Mabo Decision: 30 years on
- Marine Geophysics Laboratory
- Office of the Vice Chancellor and President
- Outstanding Alumni
- Pharmacy Full Scope
- Planning for your future
- Policy
- PAHL
- Queensland Research Centre for Peripheral Vascular Disease
- Rapid Assessment Unit
- RDIM
- Researcher Development Portal
- Roderick Centre for Australian Literature and Creative Writing
- Contextual Science for Tropical Coastal Ecosystems
- State of the Tropics
- Strategic Procurement
- Student profiles
- SWIRLnet
- TREAD
- TropEco for Staff and Students
- TQ Maths Hub
- TUDLab
- VAVS Home
- WHOCC for Vector-borne & NTDs
- Media
- Copyright and Terms of Use
- Australian Institute of Tropical Health & Medicine
- Pay review
Phishing is a relatively new phenomenon that commonly uses websites and email to steal confidential information such as credit card numbers, passwords and other information that can be used for financial gain.
Typical phishing attempts involves receiving an email on a particular topic of importance or interest such as wining a prize, taxation department refund, topical news story on a disaster or threat or to confirm financial information.
The email will often ask for some action to be performed, such as clicking on a link or providing some information.
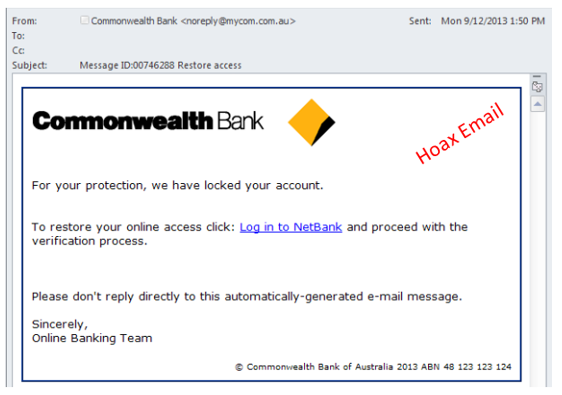
For example:
Practical tips to identify phishing emails
- Phishers may impersonate the sender making the recipient think that the original email was from a legitimate source. This could even be a JCU logo.
- The subject usually requests some action.
- There is usually an attachment or a link.
- The purpose of the email is to entice the reader to client on the web link and login or provider other personal information. If you are in doubt, report the email to your services provider.
Practical tips to avoid phishing
Luckily, avoiding phishing can be fairly straightforward, and with some reasonable caution, becoming a victim can be avoided. Here are some practical tips:
- Do NOT click on a web link in an email or open an attachment in an email unless you know and trust the sender.
- Use your mouse to hover over links to see if they are genuine.
- James Cook University will never ask you for your password or information about your account via email.
- If you receive a suspicious attachment, you can submit it to third-party virus scanning products like Virus Total for analysis.
What to do if you've clicked the link?
If you've already clicked the link and entered your details, the most important step to take is to change your JCU password immediately.
If you require assistance with changing your password or have any further enquiries then please contact the IT Help Desk.
Third Party Tools
A variety of publicly available tools are available on the internet to help you check phishing emails:
| Website | How it helps |
|---|---|
| https://www.phishtank.com/ | Check a potentially malicious URL |
| https://www.virustotal.com/ | Check a potentially malicious file or URL |